Mobile apps have made our life much easier. We are now dependent on mobile apps for the completion of many of our tasks. They are much faster and provide us instant online and offline access. We can do our daily transitions through them. IoT has also helped us a lot in this regard. To know more about such mobile apps read here.
For doing such works, our precious data like bank account details are also stored on our phones. Thus, the apps and mobile devices are big takers for spying malware to get access to data. This article explains the ways to secure mobile apps.
Some of the main points discussed in this article are:
- MAM
- Containerization
- The Code Security
- Permissions
- Prevent The Data Theft
- Managing Third Party Libraries
- The Code Testing
- Securing The Backend Networks Connection
- Least Privilege
- Proper Session Handling
- Lack Of The Binary Protection
- Detect Vulnerabilities On Runtime Environment
Why Mobile App Security Is Important
No doubt mobile apps deliver some effective services to the users, but their security is still the central question. Many apps have been hacked, and the data gets stolen. The cost of a lost mobile data is far more than the value of a failed mobile device. To get good mobile app security, you need to be aware of the policies and the mobile device management too. The mobile application security emphasizes data and not much on devices. Thus, user’s mobile privacy is indeed an important thing.

How to Get Mobile Application Security
Following are the ways by which you can secure your devices from a malicious app and the data theft.
MAM
MAM refers to the mobile application management.
- It plays a vital role in the mobile application security as it keeps the user safe form many security issues by deterring him from installing the wrong apps.
- It correctly configures the right apps.
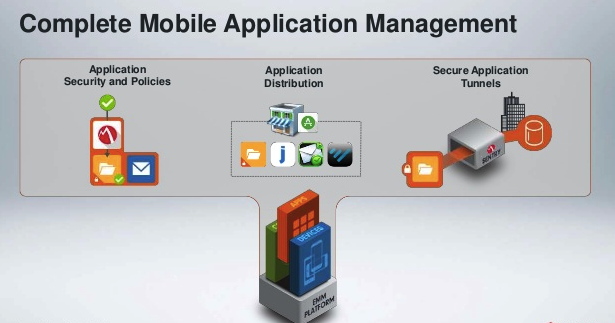
Containerization
This refers to technologies that create a trusted environment to store the business data. Such technologies create an authenticated and an encrypted environment for this purpose.
- If a device is unable to support the 2-factor authentication, then the container does this job for that device.
- If a lousy app is installed on a device, then it disables the access to that faulty app to the container.

The Code Security
Often malware is included in the code of the mobile apps.
- Before the malware gets exploited, attackers get a copy of the application code, and then they reverse engineer it.
- In this way, they transit some favorite apps into the rogue apps that contain the vulnerabilities.
- Then they post these apps on some third-party app store. In this way, they trick the user and compromise their mobile phones.
Thus, enterprises need to keep an eye on such malware in code.
They should aid their developer so that they detect the vulnerability in the apps and harden the security of those apps.

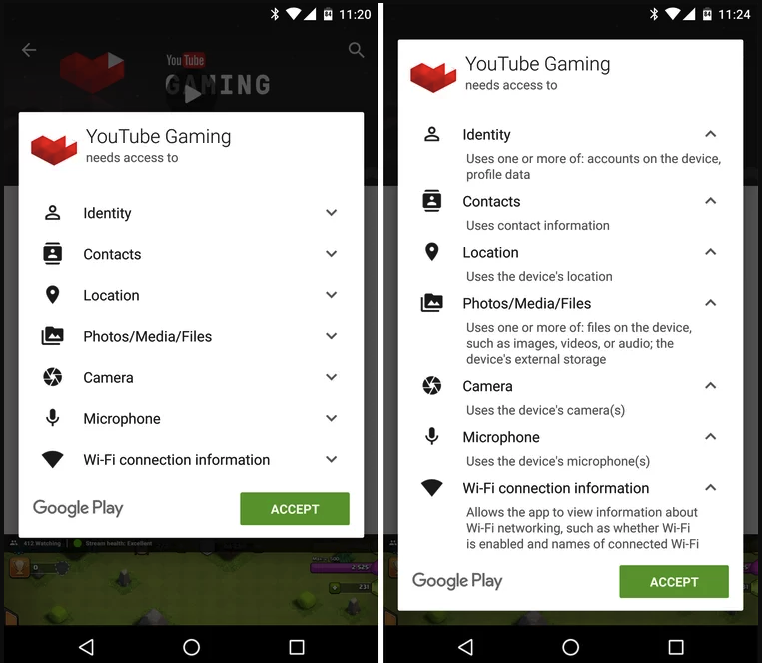
Permissions
Sometimes the user grants excessive permission to the mobile applications which result in the spread of malware in their device.
Enterprises should need to take into account the up to date sources to tackle such issues.
Prevent The Data Theft
After spreading the malware through the mobile application, the hacker immediately looks for the access to the mobile data
The data leakage is indeed a big issue.
- Enterprises need to consider the remote wipe capabilities to address the stolen devices.
- Also, mobile data encryption can be used to even the data loss from the mobile phones.
Managing Third Party Libraries
A proper system needs to be used by the developer that check for the updates in the third-party code of the developer.
- In this way, the code will be running in the current version.
- If such updates are not checked regularly, then the attackers can identify those security holes and exploit your device.

Other ways to provide mobile app security are listed below.
- The Code Testing: Run the source code scanning multiple times. This will help to figure out issues in the code.
- Securing The Backend Networks Connection: Apps API accesses the server to get the data. Such server and the cloud servers should have the security measures to protect your data.
- Least Privilege: To secure the data on your phone, you need to limit the permission requested to the critical data for the apps.
- Proper Session Handling: The sessions on the mobile phone no doubt last longer than on the ones on the desktop. The tokens need to be used instead of the device identifiers for the proper support.
- Lack Of The Binary Protection: Due to the absence of binary protection, the hacker can quickly reverse engineer the codes of the app to inject malware into it. This can result in data theft.
- Detect Vulnerabilities On Runtime Environment: The security of an application depends on a devices’ safety too. The mobile app sandbox needs to be intact.
Final Thoughts
We are now living in the age of mobility. The number of mobile phones users have now surpassed the desktop users worldwide. This demand to the applications hardening to secure the data. Employees do not own mobile phones used for business. The hackers target these mobile phones to get the data. The appropriate mobile security framework needs to be looked upon to save avoid the data leakage from the smartphones. The primary goal is to ensure the mobile phone security to safeguard the user data.
Author Bio

Allen Jame is a blogger and a web developer. Allen loves reading and writing blogs.